SA
Linux、FreeBSD、Unix、Windows
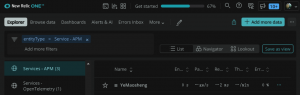
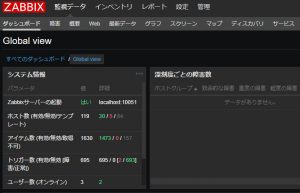
From Telegraf To NewRelic
Standard…
ConoHaオブジェクトストレージでのコンテナをWEB公開する
Standardオブジェクトの公開を行う事によりトークンを使わないでダウンロードを行う事が可能です。
誰でもアクセスできるようになるため、公開したくないファイルは注意が必要です。
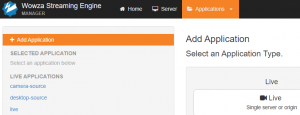
Wowza記録されたメディアをAWS S3にアップロードする
StandardInstall Nginx with RTMP Module on CentOS
StandardInstallation process …
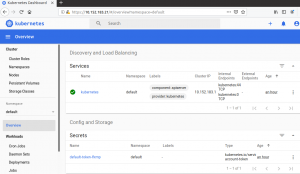
YAML file for K8S
Standard3a6408beaf5b0700bd622def2a737e31013